Why Use This Code?
Web Presentation and Text are Copyright©2017 by Daniel B. Sedory
NOT to be reproduced in any form without Permission of the Author !
Though written mainly for forensic investigators and data recovery specialists who've stumbled across the ID String at the end of the code bytes in the MBR below, anyone with enough knowledge to have looked at the hex bytes of their MBR sector may also find this useful.
When asked to look at some code found in an MBR sector and determine if there was anything malicious about it, we concluded it would load and transfer control to the Active partition's Boot Record similar to other normal MBRs; and in fact, 52 percent of its code is the same as an IBM/Microsoft DOS 3.30 MBR (shown in Green below; bytes with [brackets] around them are different from the Standard (DOS) MBR Code because the only error message is in a different location and some code was also relocated, so the offset bytes must be different).
Another 11.3 percent of the code (shown below in Light Green) is from the Windows 2000/XP MBR and byte for byte the same as its Extended Read routine.
So, at least 63 percent in
total of what you see is from DOS and Windows MBR code.
But, for FAT32 and NTFS Boot Records, the rest of the code (shown in Light Gray)
not only uses the Head and Sector values provided by the BIOS (using Interrupt 13's GET DRIVE PARAMETERS function) to possibly alter those values in
Memory, but also writes that Boot Record (all 512 bytes) from Memory back to the disk drive's Volume/Partition Boot Record! And it does this
every time the machine boots-up from this MBR; even when those bytes are identical.
Yet, for any other type of Boot Record, or more precisely:
Anything this code does not consider a FAT32 or NTFS Boot Record, execution is transferred to it in Memory without any changes nor writing the
VBR/PBR to the disk.
A short time after beginning to write about this MBR code, two great guys in the grc.security.software news group directed my attention
to a program found on the Net: MiniTool's PartitionWizard.
Well, after running a quick test, even though neither the MBR code nor the ID String
(D210A615-ACFD-414a-BDF1-FC9F2A85F076) could be seen (in the clear) in any of its files, when using only the program's
"Rebuild MBR" function, we proved that function will overwrite all of the code bytes in the MBR Sector; including all the zero bytes
between the last digit of its ID String and the beginning of the Partition Table Area, except for any
the NT Disk Signature (shown below using "xx" instead of real hex bytes).
Using any of this program's recovery tools, could easily alter the data in a drive's Partition Table, but applying the "Rebuild MBR" function,
all by itself, will not do so. This function will also write the 0xAA55 MBR Signature (0x55 and 0xAA; the last 2 bytes of the Sector) to the disk.
Note: We used an older version (4.2; from 2009) and the most recent one (10.2.1; March 23, 2017). Both wrote exactly the same bytes. From data we've seen elsewhere on the Net, we would conclude it's highly likely all versions of PartitionWizard will do the same. In their forums, a MiniTool rep recently confirmed this ID String was a result of using the "Rebuild MBR" function in their program (search page for ID String). But they were rather vague about what this code was being used for and why it needed to write a Volume/Partition Boot Sector to a disk drive every time it executes on a Windows PC.
Absolute Sector 0 (Cylinder 0, Head 0, Sector 1) Offset 0 1 2 3 4 5 6 7 8 9 A B C D E F 0000 FA 33 C0 8E D0 BC 00 7C 8B F4 50 07 50 1F FB FC .3.....|..P.P... 0010 BF 00 06 B9 00 01 F2 A5 EA 1D 06 00 00 BE BE 07 ................ 0020 B3 04 80 3C 80 74 0E 80 3C 00 75 1C 83 C6 10 FE ...<.t..<.u..... 0030 CB 75 EF CD 18 8B 14 8B 4C 02 8B EE 83 C6 10 FE .u......L....... 0040 CB 74 1A 80 3C 00 74 F4 BE[F8]06 AC 3C 00 74 0B .t..<.t.....<.t. 0050 56 BB 07 00 B4 0E CD 10 5E EB F0 EB FE BF 05 00 V.......^....... 0060 60 6A 00 6A 00 FF 76 0A FF 76 08 6A 00 68 00 7C `j.j..v..v.j.h.| 0070 6A 01 6A 10 B4 42 B2 80 8B F4 CD 13 61 61 73 0C j.j..B......aas. 0080 33 C0 CD 13 4F 75[D9]BE [F8]06 EB[BF]BE[F8]06 BF 3...Ou.......... 0090 FE 7D 81 3D 55 AA 75[B3] BF 52 7C 81 3D 46 41 75 .}.=U.u..R|.=FAu 00A0 07 47 47 80 3D 54 74 11 BF 03 7C 81 3D 4E 54 75 .GG.=Tt...|.=NTu 00B0 40 47 47 81 3D 46 53 75 38 60 B4 08 B2 80 CD 13 @GG.=FSu8`...... 00C0 BF 1A 7C FE C6 8A D6 32 F6 89 15 4F 4F 83 E1 3F ..|....2...OO..? 00D0 89 0D 61 60 6A 00 6A 00 FF 76 0A FF 76 08 6A 00 ..a`j.j..v..v.j. 00E0 68 00 7C 6A 01 6A 10 B4 43 B2 80 8B F4 CD 13 61 h.|j.j..C......a 00F0 61 8B F5 EA 00 7C 00 00 45 72 72 6F 72 21 00 44 a....|..Error!.D 0100 32 31 30 41 36 31 35 2D 41 43 46 44 2D 34 31 34 210A615-ACFD-414 0110 61 2D 42 44 46 31 2D 46 43 39 46 32 41 38 35 46 a-BDF1-FC9F2A85F 0120 30 37 36 00 00 00 00 00 00 00 00 00 00 00 00 00 076............. 0130 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0140 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0150 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0160 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0170 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0180 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0190 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 01A0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 01B0 00 00 00 00 00 00 00 00 xx xx xx xx 00 00 00 00 ................ 01C0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 01D0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 01E0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 01F0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 55 AA ..............U. 0 1 2 3 4 5 6 7 8 9 A B C D E F |
If you no longer need Partition Wizard, and are using almost any recent Windows OS (from XP SP3 on!) on a Desktop workstation, we'd recommend using a Microsoft® Windows™ utility or other approved program to place the official MBR code for your OS back into the MBR Sector of your disk. And, in fact, trying to use this code in the MBR of many Laptops and brand-name PCs with special keyboard features during boot-up, could cause those features to no longer function. The program's "Rebuild MBR" function, as stated by the company itself, should only be used on a 'damaged' (corrupted MBR code) disk that will no longer boot.
Note: Most drives today will have the full Sector count of 0x3F (or 63 decimal) and a Head count of 0xFF (or 255 decimal). If you see something other than those values in your Boot Record, you may be dealing with an old (as in IDE) Laptop drive or a VERY small (as in only MegaBytes) disk drive which requires a different CHS geometry than what's most often found on drives today. (Also keep in mind that a USB stick, camera memory card, etc. might require a Boot Sector in its first sector; not an MBR, i.e., the whole device should be formatted like a single FAT or FAT32 volume, not a disk drive.)
With the exception of the single byte F8h at Memory location 0x649 (offset 0x49 in the MBR sector), the following code (at offsets 0x00 through 0x5F in the MBR) is identical to that found on our Standard MBR page:
7C00 FA CLI 7C01 33C0 XOR AX,AX 7C03 8ED0 MOV SS,AX 7C05 BC007C MOV SP,7C00 7C08 8BF4 MOV SI,SP 7C0A 50 PUSH AX 7C0B 07 POP ES 7C0C 50 PUSH AX 7C0D 1F POP DS 7C0E FB STI 7C0F FC CLD 7C10 BF0006 MOV DI,0600 7C13 B90001 MOV CX,0100 7C16 F2 REPNZ 7C17 A5 MOVSW 7C18 EA1D060000 JMP 0000:061D 061D BEBE07 MOV SI,07BE 0620 B304 MOV BL,04 0622 803C80 CMP BYTE PTR [SI],80 0625 740E JZ 0635 0627 803C00 CMP BYTE PTR [SI],00 062A 751C JNZ 0648 062C 83C610 ADD SI,+10 062F FECB DEC BL 0631 75EF JNZ 0622 0633 CD18 INT 18 (BIOS ROM Basic) 0635 8B14 MOV DX,[SI] 0637 8B4C02 MOV CX,[SI+02] 063A 8BEE MOV BP,SI 063C 83C610 ADD SI,+10 063F FECB DEC BL 0641 741A JZ 065D 0643 803C00 CMP BYTE PTR [SI],00 0646 74F4 JZ 063C ; The byte F8h (at 0x649) differs from the Standard MBR code since ; it must point to a different location for its only error message: 0648 BEF806 MOV SI,06F8 ; -> "Error!" 064B AC LODSB ; Load byte at [SI] into AL ... ; and increment the SI value. 064C 3C00 CMP AL,00 064E 740B JZ 065B 0650 56 PUSH SI 0651 BB0700 MOV BX,0007 0654 B40E MOV AH,0E 0656 CD10 INT 10 (BIOS Video) 0658 5E POP SI 0659 EBF0 JMP 064B 065B EBFE JMP 065B ; Infinite Loop. You must ; power-down or Reboot! 065D BF0500 MOV DI,0005 ; This instruction ensures ; the following code will ; also read from a drive FIVE times _if a read error occurs_; ; just like the _old_ IBM/MS-DOS code used to do.
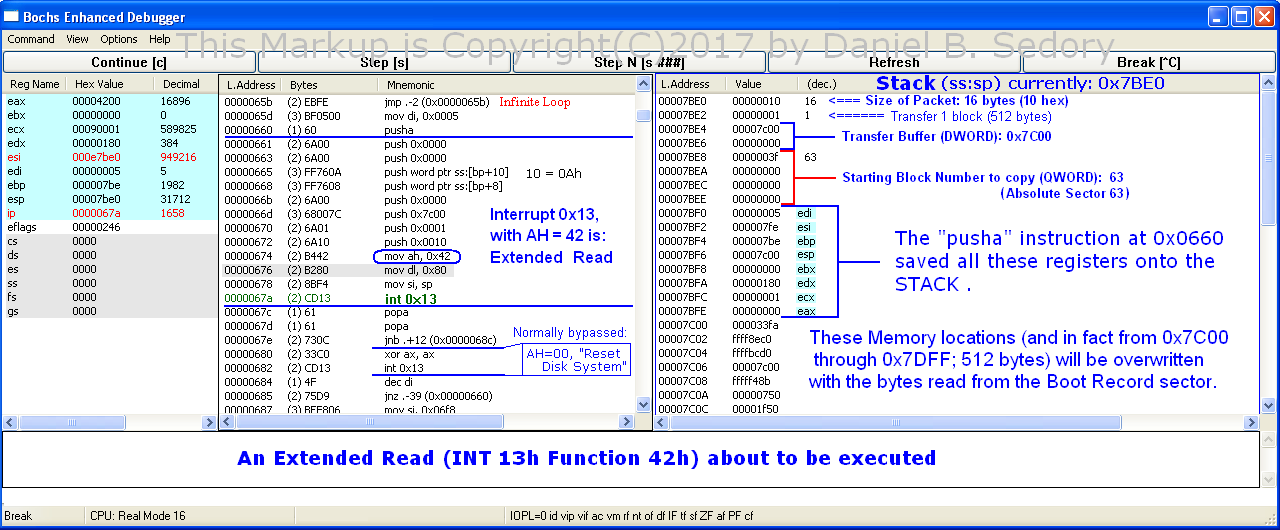
The following code, with the exception of the 2 bytes at locations 0x676-677 (MOV DL,80), are identical to the Windows 2000/XP MBR routine for an Extended Read Function. Note, however, this MBR's code never checks to see if that function is available, as the Microsoft code does, but simply assumes both Extended Read and Write Functions exist in the PC's BIOS:
0660 60 PUSHA
0661 6A00 PUSH 0000
0663 6A00 PUSH 0000
0665 FF760A PUSH WORD PTR [BP+0A]
0668 FF7608 PUSH WORD PTR [BP+08]
066B 6A00 PUSH 0000
066D 68007C PUSH 7C00
0670 6A01 PUSH 0001
0672 6A10 PUSH 0010
0674 B442 MOV AH,42
0676 B280 MOV DL,80 ; Assumes only 1st drive can boot
0678 8BF4 MOV SI,SP
067A CD13 INT 13 (BIOS Disk)
067C 61 POPA
067D 61 POPA

Here, the code resumes with bytes from the Standard MS-DOS 3.30 MBR; with the exception of some bytes that had to be changed due to the code being located at different offsets from where it was in the original DOS MBR. It's likely the author(s) began with the 'Standard MBR' as their template; making changes where necessary to fit the purposes we've noted above and below (i.e., using BIOS data for Head and Sector values of only FAT32 or NTFS Boot Sectors, and writing those to the VBR on the disk drive).
067E 730C JNB 068C 0680 33C0 XOR AX,AX 0682 CD13 INT 13 (BIOS Disk) 0684 4F DEC DI 0685 75D9 JNZ 0660 ; Here, the location of the error message points to 0x6F8: 0687 BEF806 MOV SI,06F8 ; -> "Error!" 068A EBBF JMP 064B 068C BEF806 MOV SI,06F8 068F BFFE7D MOV DI,7DFE 0692 813D55AA CMP WORD PTR [DI],AA55 0696 75B3 JNZ 064B
Here's where the code becomes much different than any official DOS or Windows MBR code:
; The code below is looking for the string "FAT" in a specific ; location within the VBR/PBR sector it loaded into Memory: 0698 BF527C MOV DI,7C52 069B 813D4641 CMP WORD PTR [DI],4146 ; "FA" 069F 7507 JNZ 06A8 06A1 47 INC DI ;\These make DI=7C54 06A2 47 INC DI ;/ 06A3 803D54 CMP BYTE PTR [DI],54 ; "T" 06A6 7411 JZ 06B9
Note the locations of 0x7C52 through 0x7C54 where it is looking for the string "FAT" in Memory (and of course, from the disk drive's Volume Boot Record). MiniTool's programmer seems to have relied on observations that this occurs there for a FAT32 volume; the full string actually being 8 bytes long: "FAT32 " (including the 3 spaces). A FAT16 volume does not have the same structure. However, official Microsoft documentation from the time the FAT32 Boot Sector was created, stated you should not rely on this (see note at Offset 52h and References on our MSWIN4.1 OS Boot Record page).
; If the above fails, then it proceeds with checking if ; the VBR sector is for an "NTFS" file system: 06A8 BF037C MOV DI,7C03 06AB 813D4E54 CMP WORD PTR [DI],544E ; "NT" 06AF 7540 JNZ 06F1 06B1 47 INC DI ;\ These make DI=7C05 06B2 47 INC DI ;/ 06B3 813D4653 CMP WORD PTR [DI],5346 ; "FS" 06B7 7538 JNZ 06F1 ; If not FAT32 nor NTFS jump to VBR. ; If either a FAT32 or NTFS Boot Record is found, then the code gets the ; Head and Sector values computed by the BIOS for the first drive (DL=0x80) ; using the GET DRIVE PARAMETERS Function (08h) of INT 13h: 06B9 60 PUSHA 06BA B408 MOV AH,08 06BC B280 MOV DL,80 06BE CD13 INT 13 (BIOS Disk) ; Then those values (which INT13 placed into part of DH and CX) ; are moved into the Boot Record already loaded into Memory: 06C0 BF1A7C MOV DI,7C1A ; Location of Head Count in VBR 06C3 FEC6 INC DH ; Head Count = Head Value + 1 06C5 8AD6 MOV DL,DH 06C7 32F6 XOR DH,DH 06C9 8915 MOV [DI],DX 06CB 4F DEC DI ;\ Makes DI = 7C18 06CC 4F DEC DI ;/ 06CD 83E13F AND CX,003F ; Sector size is < or = 3Fh. 06D0 890D MOV [DI],CX ; Copy it to 7C18 in VBR. 06D2 61 POPA ; But instead of simply proceeding to transfer control ; to the possibly altered Volume/Partition Boot Record ; in Memory, it first goes on to actually WRITE that VBR ; to the Boot Record stored on the disk drive (and does ; so every time this code is run from the drive's MBR; ; it never bothers to check if it's the same or not): 06D3 60 PUSHA 06D4 6A00 PUSH 0000 06D6 6A00 PUSH 0000 06D8 FF760A PUSH WORD PTR [BP+0A] 06DB FF7608 PUSH WORD PTR [BP+08] 06DE 6A00 PUSH 0000 06E0 68007C PUSH 7C00 06E3 6A01 PUSH 0001 06E5 6A10 PUSH 0010 06E7 B443 MOV AH,43 06E9 B280 MOV DL,80 06EB 8BF4 MOV SI,SP 06ED CD13 INT 13 (BIOS Disk) 06EF 61 POPA 06F0 61 POPA
06F1 8BF5 MOV SI,BP 06F3 EA007C0000 JMP 0000:7C00 <-- Jumps to Boot Sector code in Memory.
Offset 0 1 2 3 4 5 6 7 8 9 A B C D E F 06F0 45 72 72 6F 72 21 00 44 a....|..Error!.D 0700 32 31 30 41 36 31 35 2D 41 43 46 44 2D 34 31 34 210A615-ACFD-414 0710 61 2D 42 44 46 31 2D 46 43 39 46 32 41 38 35 46 a-BDF1-FC9F2A85F 0720 30 37 36 076
Updated: May 12, 2017 (2017.05.12; internally); May 18, 2017 (2017.05.18);
May 24, 2017 (2017.05.24).
Last Update: May 25, 2017.
(2017.05.25)
You can write to us here: contact page (opens in a new
window).![]() MBR and Boot Records Index
MBR and Boot Records Index
![]() The Starman's Realm Index Page
The Starman's Realm Index Page